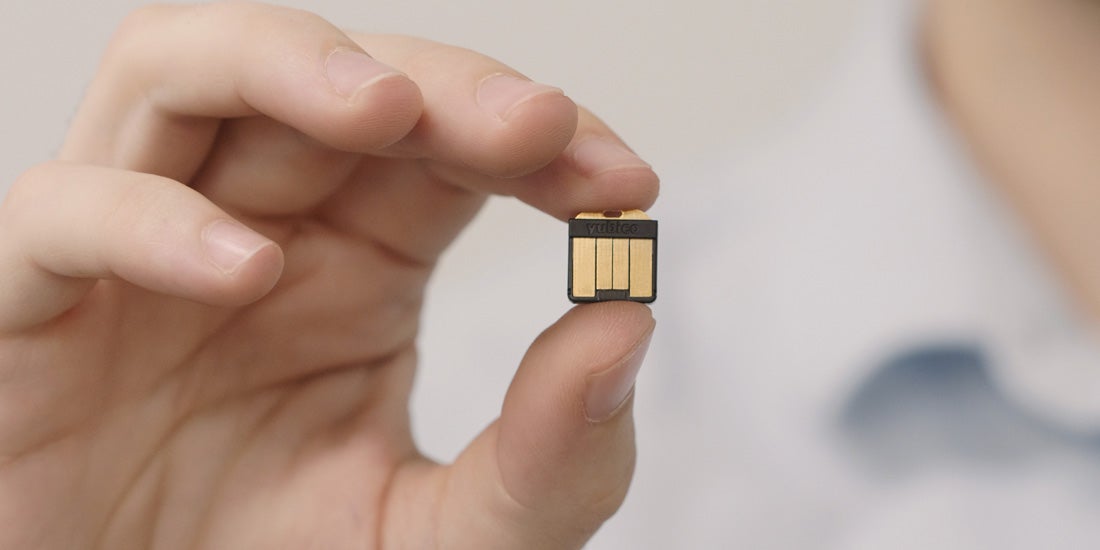
As the rate and complexity of credential theft and phishing attacks on enterprises continue to increase rapidly, so do the number of server-based attacks. YubiHSM 2, the leading nano-form factor hardware security module (HSM), offers organizations superior protection from these attacks for sensitive data against theft and misuse. The new YubiHSM 2 (v2.4) – officially available on Monday, September 9 – brings key updates that are designed to increase data security across hybrid and multi-cloud environments, and is a significant step forward enabling organizations to address increasing sophisticated cybersecurity challenges and move toward a phishing-resistant enterprise.
The world’s smallest hardware security module enables organizations to securely and cost-effectively store and transfer data in a multi-cloud environment using an on-premises HSM for secure management of cryptographic credentials – at a fraction of the cost and size of traditional HSMs. YubiHSM 2 is a full-function, network accessible HSM with a rich cryptography suite, PKCS#11 interface, software development kit, and tools. YubiHSM 2 is made available in a nano form-factor that easily fits into a USB-A port on a server, offering a low-cost alternative to traditional HSM models, which come in a variety of form factors including rack mounted hardware and may cost tens of thousands of dollars in upfront and year-over-year maintenance costs.
The new capabilities in YubiHSM 2 (v2.4) provide a number of benefits to organizations looking for portable security in multi-cloud environments. Let’s get into the exciting new and expanded features below.
YubiHSM 2 (v2.4) now enables backups using asymmetric cryptography
Backing up sensitive data from one HSM to another is an extremely security sensitive operation that generally requires an air-gapped security environment when symmetric cryptography is used for data encryption. This requires the symmetric key to be exposed for a short period of time so that it can be shared between the primary and the backup HSM. A compromised symmetric key can expose sensitive data to would-be attackers.
With YubiHSM 2 (v2.4), we have introduced the ability to wrap sensitive data in the YubiHSM 2 for backup using asymmetric cryptography. By using asymmetric cryptography, we can ensure that no secrets are exposed even if wrapped data is sent over the internet to another location for backing up.
‘Bring Your Own Key’ support
To enable organizations to own and manage their own encryption keys in multi-cloud environments, we have introduced support for ‘Bring Your Own Key’ (BYOK). This YubiHSM 2 (v2.4) capability enables organizations to securely and cost-effectively store and transfer data in a multi-cloud environment using an on-premises HSM for secure management of cryptographic credentials – enabling regulatory compliance, enhanced data security in a multi-cloud environment, better control, portability and flexibility, at a fraction of cost of traditional on-premises HSMs.
For more information on the BYOK support, visit the initial blog post here. To learn more about YubiHSM 2 and the benefits it provides businesses, visit here.
YubiHSM 2 + Yubico’s cryptographic library
Aligned with the recent updates in the YubiKey 5.7 release, YubiHSM 2 (v2.4) takes advantage of Yubico’s in-house developed cryptographic library that performs the underlying cryptographic operations (decryption, signing, etc.) for RSA and ECC.