Resources
Browse our library of white papers, webinars, case studies, product briefs, and more.
-

YubiEnterprise Delivery solution brief YubiEnterprise Delivery supports teams to deliver to users globally. Read more -

Yubico Enterprise solutions brief Modern authentication and security for the digital enterprise. Read more -

YubiKey 5Ci product brief The first dual connector YubiKey, supporting USB-C and Lightning connectors. Read more -

Support Services solution brief Industry leading support and integration services to ensure your YubiKey program is a success. Read more -

Portable root of trust for government The YubiKey is a portable root for remote workers, non PIV/CAC eligible workers, mobile/BYOD, and shared devices/workstations. Read more -

Public Sector Brief Getting started with YubiEnterprise Services YubiEnterprise Subscription is a service-based and affordable model for purchasing YubiKeys. Read more -
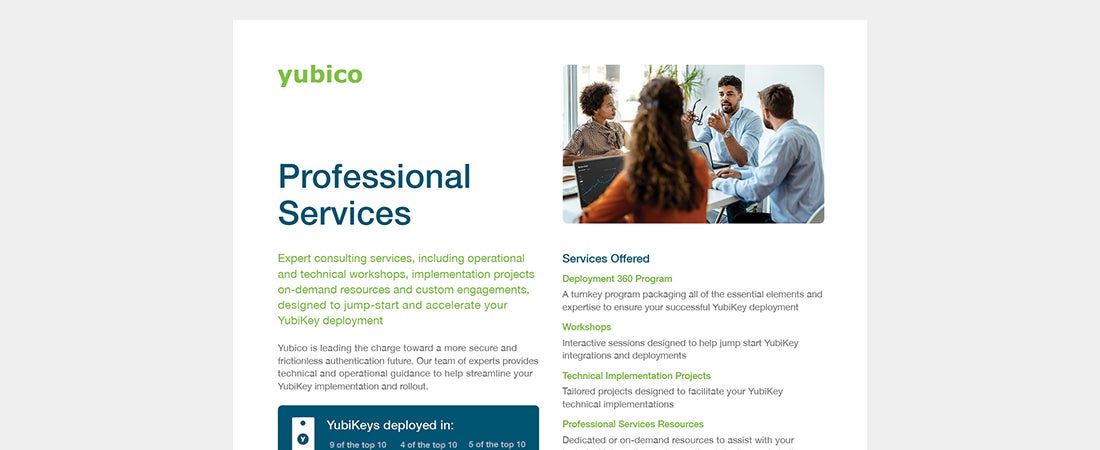
Professional Services Solutions Brief Come learn about our expert consulting services: workshops, implementation packages, on-demand assistance and more. Read more -

PrimeKey partner brief PrimeKey and Yubico together simplify and secure the management of cryptographic keys. Read more -

PrimeKey + Intercede partner brief Best practice lifecycle management and security for hardware-protected cryptographic keys. Read more