Cyberattacks and a shifting regulatory environment
Organizations are facing an unprecedented level of disruption to supply chains, from the global pandemic and the economic recession, to port disruptions and record high freight costs. Hackers now specifically target third-party systems, software, code or IP. In fact, up to 97% of organizations have had a cybersecurity breach as the result of a weakness in the supply chain. Disruptions to the supply chain can compromise the integrity of the products or services being delivered or the security and privacy of the data or code being exchanged which can lead to delays in business operations and reduced bottom lines across all industries.
In response to increased threats to the supply chain and critical infrastructure sectors, the White House Executive Order (EO) 14028 and Office of Management and Budget (OMB) Memo M-22-09 introduced new expectations and guidelines for Zero Trust and phishing-resistant multi-factor authentication (MFA) for federal agencies and enterprises— as well as their suppliers and partners.
Organizations can begin their journey to reducing risk across the supply chain at all levels, by identifying and mitigating risk in three key areas:
Key areas to identify and mitigate risk

Third-party access

IP and product integrity
Software supply chain
Securing supply chain access with modern, phishing-resistant MFA
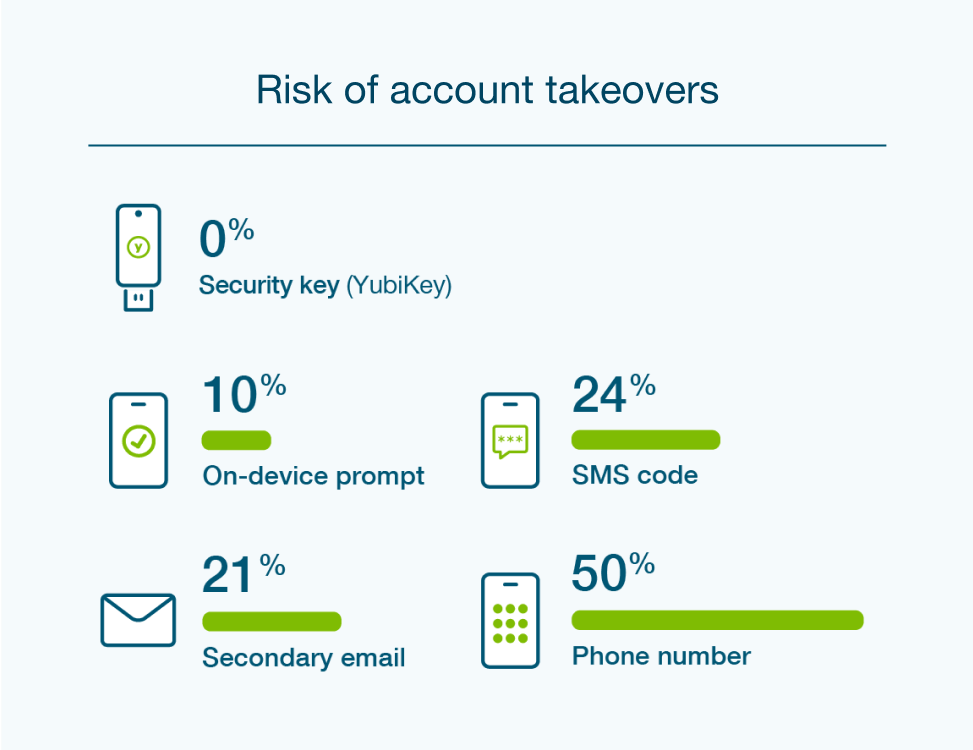
Organizations must identify and authenticate every user who has access to inputs, IP, or to the systems involved in the supply chain. One of the top recommendations in the updated NIST 800-161, Cyber Supply Chain Risk Management Practices for Systems and Organizations, is to employ multifactor authentication to safeguard remote and third-party access to the network. However, not all MFA is created equal, nor is all MFA considered phishing-resistant. OMB M-22-09 defines phishing-resistant MFA as an authentication process that is immune to attackers intercepting or even tricking users into revealing access information.
Phishing-resistant MFA

Federal Government’s Personal Identity Verification (PIV) standard

FIDO2/WebAuthn
Not phishing-resistant MFA

Passwords

SMS and other one-time passwords (OTP)

Security questions

Mobile push apps
The YubiKey from Yubico provides phishing-resistant multifactor and passwordless authentication at scale across the supply chain, helping organizations and their suppliers implement robust, easy-to-use authentication for any user who has upstream access to the network or at critical IP handoffs.
The YubiKey is the only solution that is proven to stop 100% of account takeovers in independent research. Further, the YubiKey offers an unparalleled user experience, a tap-and-go passwordless experience that is 4x faster than SMS and offers a 92% reduction in support calls. YubiKeys are also available in FIPS 140-2 validated form factors.