Modern authentication for the Army
How the YubiKey complements the CAC and solves U.S. Army modernization use cases with phishing-resistant MFA
MFA evolution across the Department of Defense
Using the Common Access Card (CAC) for authentication is not always practical for every U.S. Army soldier, civilian employee, contractor, or mission partner. Guidance such as the National Security Memorandum/NSM-8, and more importantly, cyber attacks from nation-states to criminal organizations have put pressure on the DoD to deploy phishing-resistant authentication as part of a Zero Trust Architecture and created requirements to modernize authentication across the entire Department of Defense (DoD).
While CAC meets the highest assurance of MFA when using DoD Public Key Infrastructure (PKI), there are a growing number of scenarios that have the same assurance requirements where CAC is not available or practical. These scenarios include secure access for telework, BYOAD (Bring Your Own Approved Devices), non-CAC eligible coalition and mission partner environments, air-gapped/isolated networks, shared devices and tactical scenarios overseas where relying on a CAC may inadvertently reveal identities. For example, CAC reader support for mobile phones or tablets is limited or non existent, and teleworking with a CAC reader leaves the device open to potential malware.
There is a growing need for cost-effective, turnkey solutions to address the needs of today and future-proof against the authentication needs of tomorrow— including those currently under DoD policy review such as Fast Identity Online (FIDO) authentication standards.
Not all MFA is created equal
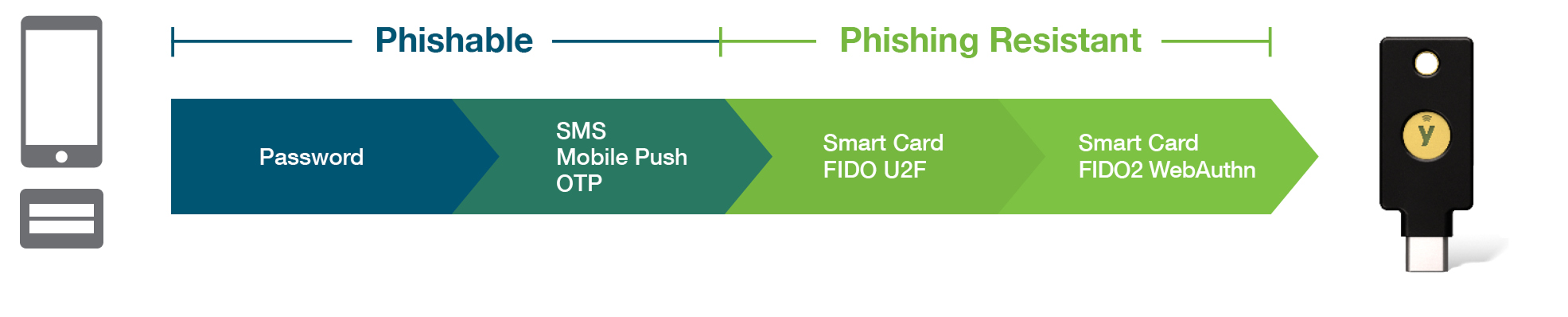
For those use cases where the CAC is limited or not practical, falling back on username and passwords or legacy multi-factor authentication (MFA) is risky. Usernames and passwords are easily phished, and legacy mobile-based authentication such as OTP, SMS and push notification apps are also not phishing resistant. Accounts using MFA that are not based on phishing-resistant protocols are susceptible to having credentials stolen.
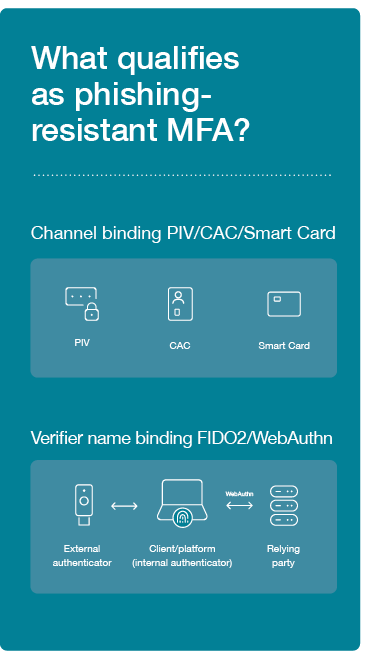
The draft National Institute of Standards and Technology (NIST) Digital Identity Guidelines (SP 800-63-4), designed to guide agencies with digital identity assurance and authentication, outlines the technical requirements for phishing-resistant authentication, recognizing two methods as being phishing-resistant: channel binding such as using a PKI-based Smart Card and verifier name binding such as using a Fast Identity Online (FIDO)-based credential and authenticator.

What is Fast Identity Online (FIDO)?
FIDO2 is an open authentication standard, created by the FIDO Alliance, that consists of the W3C Web Authentication specification (WebAuthn API), and the Client to Authentication Protocol (CTAP). CTAP is an application layer protocol used for communication between a client (browser) or a platform (operating system) with an external authenticator such as a hardware security key. FIDO2 authentication options include strong single factor (passwordless), two-factor, and multi-factor authentication. Yubico is a core contributor to the FIDO2 open authentication protocol.
The YubiKey offers FIPS-validated phishing-resistant MFA
Yubico offers the phishing-resistant FIPS 140-2 validated YubiKey, a DoD-approved hardware security key that offers highest-assurance multi-factor and passwordless authentication in accordance with Homeland Security Presidential Directive 12 (HSPD 12). The YubiKey is approved for use as an MFA authenticator for DoD Unclassified and Secret information systems that can meet use cases where the CAC is not available nor practical, by leveraging derived CAC credentials. The DoD OCIO Memo on Mobile Public Key Infrastructure (PKI) Credentials, 19 December 2019, approved the YubiKey as a mobile authenticator for issuance of DoD Mobile PKI credentials.
The YubiKey supports derived credentials and provides the highest levels of security needed to protect against modern day attacks along with the flexibility to secure even the most complex scenarios—from air-gapped networks to remote work and cloud services—all from a single key. With multi-protocol support including Smart Card (CAC), FIDO U2F, FIDO2, OTP and OpenPGP, the YubiKey supports both legacy and modern architectures with a single solution, and offers a future-proofed bridge to modern FIDO authentication standards.
A single YubiKey can provide both PKI and FIDO2/WebAuthn phishing-resistant authentication to securely authenticate users to applications and services across GFE or personal devices such as laptops, desktops, tablets, and mobile phones. Unlike managing multiple certificates across mobile devices and CACs, a YubiKey with Purebred derived credentials can be used as a portable root of trust across multiple devices including mobile and BYOD/BYOAD. A single YubiKey can provide both PKI and FIDO2/WebAuthn phishing-resistant authentication, housing multiple of each credential. By meeting DoD mobile PKI credential storage requirements, a YubiKey can hold either DoD PKI credentials, issued by Purebred, or an organization can host their own PKI to provide credentials to non-CAC eligible personnel, or for air-gapped and other accepted networks.
Securing privileged users

Ensuring secure phishing-resistant user access to classified, secret and personal information is critical for those privileged users that cannot use the CAC to authenticate. The YubiKey offers the highest-assurance alternate authentication that can be used to authenticate privileged users to both legacy and modern applications. The YubiKey’s hardware design enables the authentication secret to be stored on a secure hardware chip that cannot be copied or stolen, offering the highest security for authenticating privileged users. The YubiKey can be used for step-up authentication for high-security applications.
A top priority for CIOs across the DoD is to ensure strong MFA in air-gapped or Research and Development Testing and Evaluation (RDT&E) networks that cannot take advantage of the high assurance of DoD PKI. These environments require innovation and creativity to add strong MFA for network admins, end users, and other privileged roles.
DoD Microsoft 365 tenant admins cannot use their primary DoD credentials to authenticate for daily tasks and maintenance. Microsoft Azure supports the enrollment of a YubiKey as a FIDO2 authenticator. Admins are able to quickly enroll a YubiKey for their privileged user roles to meet phishing-resistant authentication requirements. A YubiKey as a FIDO2 token uses public/private keypairs, bound to the tenant URL, to ensure strong authentication is met.
Securing mission partners

Coalition and “five-eyes” (FVEY) mission partners use PKI credentials to authenticate to DoD systems, but mission partners are not always CAC-eligible. YubiKey is a solution that the Army can uniquely manage at the unit level to support access to the data needed to conduct missions, support strong and phishing resistant authentication for mission partners at the tactical edge.
A YubiKey, as a multi-protocol authenticator, provides flexibility and personalization to coalition networks that require DoD credentials for mission partners. Coalition networks can generate and manage local credentials, provision them to a YubiKey, and issue them to mission partners requiring access to DoD resources within a respective Area of Responsibility. This will ensure that only locally issued credentials can be used for authentication within the respective Combatant Command network. Additionally, options are available for the type of managed credentials — tactical PKI supports certificate-based credentials while other ICAM components can issue FIDO2 credentials. Both types of credentials meet phishing-resistant authentication requirements.
Securing telework & BYOAD

Supporting teleworkers and BYOD using the CAC creates complexity. While password-based authentication may simplify remote access, relying on single-factor authentication does not satisfy zero trust security and phishing-resistant authentication requirements.
Fortunately, YubiKey works with leading Identity and Access Management (IAM) and Identity Provider (IdP) solutions to enable phishing-resistant access for remote and hybrid employees without the need for supporting devices. For Army soldiers, civilian employees, contractors, and mission partners, this offers reliable, flexible, and trusted access to Army resources using Purebred derived certificates. Amazing capabilities such as Microsoft Azure Virtual Desktop that make it easier for service members to access services from home, no longer need to be reliant on a CAC and a separate CAC reader. In cases where remote and hybrid workers are sent GFE devices, the YubiKey can also be used as a portable root of trust to ensure the device hasn’t been compromised enroute.
YubiKeys have the flexibility to be used with a wide range of mobile devices and unmanaged and managed workstations, including Chromebooks and personal phones. When a YubiKey has been provisioned with DoD Purebred credentials, it becomes a portable root of trust for service members’ identities, making it easier to authenticate regardless of the device.
Securing shared devices & workstations

Army soldiers, civilian employees, contractors, and mission partners that use shared workstations and shared devices can benefit from using the YubiKey as a portable root of trust for secure authentication. They can authenticate to the network using the trusted Smart Card credential on their YubiKey, proving they are a trusted user.
A single YubiKey works across multiple shared devices including desktops, laptops, mobile, tablets, and notebooks, enabling users to utilize the same key as they navigate across devices. YubiKeys are also easily re-programmed, making them suitable for rotating-shift and temporary users across these environments.
The use of shared workstations and mobile devices are increasingly common across the Army. By affording a pool of resources for Army soldiers, civilian employees, contractors, and mission partners, the Army can lower the total cost of ownership of devices. However, shared devices still have the challenge of supporting multiple users, each requiring DoD credentials for authentication. By shifting the storage of the credentials from the device to a hardware-based authenticator, like a YubiKey, each individual can be issued a security key for authentication on any of the shared devices. Users do not have to worry about grabbing the right devices matching their stored soft credentials.
Securing non-CAC eligible users

Non-CAC eligible personnel such as dependents, contractors and other users that require 3rd party access still require secure access to Army systems. To meet these needs, the DoD approved the YubiKey as one of three alternate MFA solutions when PKI is infeasible—a FIPS 140-2 validated alternative to the CAC that allows non-CAC personnel or personal non-GFE devices in a BYOD environment to securely authenticate to DoD networks.
Securing office workers

The Army’s deployment of Azure Virtual Desktop (AVD) has been welcomed with open arms by Active Guard and Reserve service members. Army personnel can easily use the YubiKey for access to AVD regardless of the device being used to connect. Having a provisioned YubiKey offers flexibility to use both office desktops and personal laptops for access to AVD, providing a strong productivity workflow for daily tasks. The YubiKey comes in multiple form factors and can be used across desktops, laptops, and mobile devices without the need for an additional smart card reader peripheral device.
Securing SCIFs & air-gapped networks

Air-gapped networks are closed off from the outside, making it difficult to authenticate users using data sent over a network. Many air-gapped systems still use a username and password or a combination of passwords and a digital identity. The multi-protocol capability of YubiKeys ensures that air-gapped networks stay secured against breaches by providing phishing-resistant MFA options that work well in isolated network and mobile restricted environments as they don’t need any network connectivity, cellular connection, or batteries to work. YubiKeys are compatible with Cross Domain Solution (CDS) and Multi-Level Security (MLS), and users can be authenticated without transfer of information.
Ready to get started?
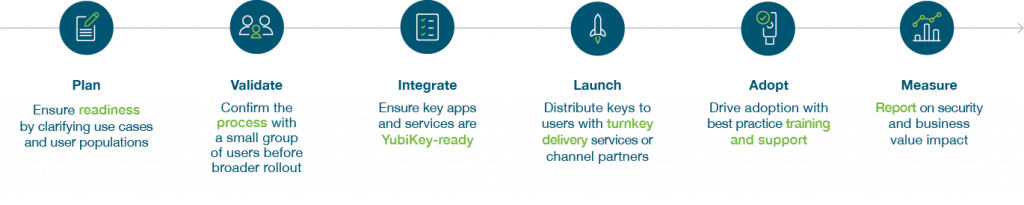
When you choose YubiKeys as a service, you make decisions as you go with our insight and help, simplifying the process of scaling YubiKeys to wider circles of use cases and leveraging the insight from over 150 U.S. government implementations to date.
We have created a six step deployment process to plan for and accelerate adoption of phishing-resistant MFA at scale. Agencies can obtain Not for Resale (NFR) YubiKeys for proof of concept (POC) programs. Yubico also offers solutions engineering support for architecture design and review, and IDP configuration guidance through the POC.