Drive business continuity and cyber resilience with modern FIDO security keys
Ensure business continuity and cyber resilience with phishing-resistant users
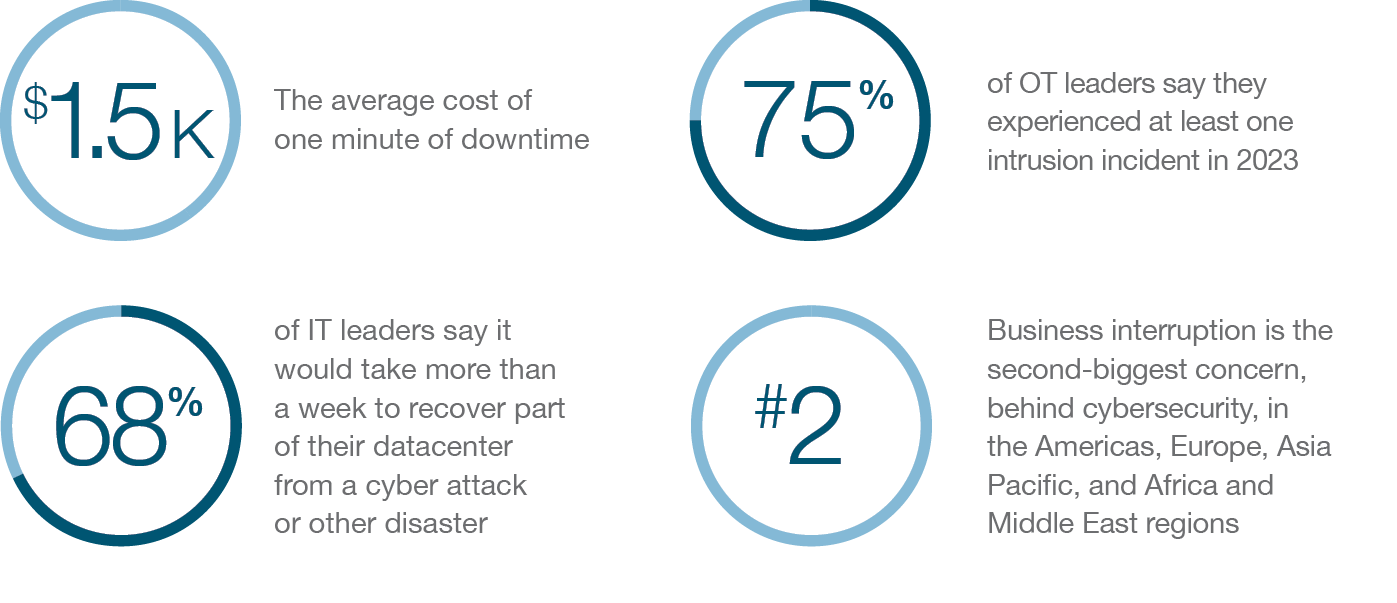
Half of organizations have suffered a cyber attack or incident that prevented access to data in 2023.1 While cyber attacks are the biggest cause of outages, business continuity also suffers when there’s an issue with your infrastructure, application software, cloud resources, and more. With most cyber attacks, malicious actors don’t break in, they log in—using stolen credentials acquired through phishing.
It is imperative that organizations deploy highest-assurance, phishing-resistant authentication across the entire user lifecycle, including registration, authentication and recovery processes, to create phishing-resistant users.
How do you create phishing-resistant users?
Choosing the best FIDO approach:
Based on NIST guidelines, currently only multi-factor authentication (MFA) based on Smart Card or FIDO2 (passkeys) is considered phishing resistant. And if you are going the FIDO route, depending on the FIDO authenticator you choose, it can also help you maintain business continuity in a variety of scenarios.

FIDO solutions such as platform authenticators (i.e. fingerprint scanners built into devices) may provide all the perceived security you need most of the time. But there are use cases where it isn’t enough. If you are like most people you want to authenticate from many devices. Each of these devices would need to register and securely store the passkey which can be time consuming and difficult to remember where all the passkeys are stored.

To have the highest level of assurance, passkeys need to be stored in hardware-based secure elements. Leveraging a security key to authenticate across all your devices allows you to be productive while providing the highest level of security. Plus, FIDO hardware security keys offer portability which drives productivity for users that use multiple devices and doesn’t leave credentials on all the devices that a user has used in the pastTo have the highest level of assurance, passkeys need to be stored in hardware-based secure elements. Leveraging a security key to authenticate across all your devices allows you to be productive while providing the highest level of security. Plus, FIDO hardware security keys offer portability which drives productivity for users that use multiple devices and doesn’t leave credentials on all the devices that a user has used in the past.
Always-on enterprises with the phishing-resistant YubiKey
The YubiKey is a modern multi-protocol hardware security key supporting Smart Card (PIV) and FIDO, that contains the highest-assurance passkeys for phishing-resistant MFA, and passwordless authentication at scale. Rest assured that with the YubiKey you deploy the most secure passkey strategy: device-bound that is purpose-built for security, Authenticator Assurance Level 3 (AAL3) compliant, and FIPS 140-2 Level 2 and Level 3 validated.
Because the YubiKey doesn’t need regular firmware patches, batteries, or even an internet connection to work, it’s always-on to keep your business running—helping you to be cyber resilient. Even if your employees don’t use their YubiKey every day, having one available enables them to securely log on to perform their daily tasks, until they are re-registered across all services.
The YubiKey supports business continuity and enables cyber resilience across common business scenarios to keep your employees and your business secure and up and running 24×7:

Privileged users
Engineers, IT and security admins, C-Suite, HR, finance, and sales

Remote staff
office workers, & field technicians

Users across supply chain
Contractors, contract service workers, secondees and joint ventures

Shared workstation environments

OT and mobile-restricted environments

Customer accounts

Whether you are securing employees in an industrial environment or corporate office, or protecting a sea of external vendors or high-value customers, with the YubiKey you can secure user access and accounts for anyone, anywhere and across any industry. You are cultivating phishing-resistant users.
“Attackers see value in gaining access to any Datadog account. Deploying YubiKeys at scale gives us the trust and peace of mind that only our employees are able to access our systems.”

“Proactively securing our global supply chain was an important step as properly tested and approved products are counted on by our customers who buy and deploy them.”
