Every day, YubiKey users are protecting access to their data in cloud services like Gmail, Dropbox, and password managers, but these very same people also need to protect access to desktop and laptop computers as well. Thanks to the multi-protocol capabilities of the YubiKey, they can. The YubiKey can be used to log in to Linux, Mac, or Windows machines.
One of the more popular use cases we hear about is logging into Windows machines, which is why we designed the Yubico Login for Windows Application. The tool provides a simple and secure method for YubiKey users to secure access to their Windows computers. Today, we are opening the public preview program for the application.
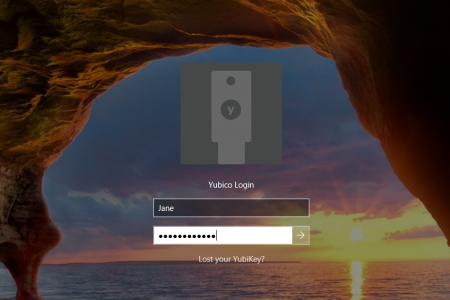
The Yubico Login for Windows Application will deliver a simplified configuration experience, enabling users to help protect their computers with a YubiKey. In addition, this application will enable new core features such as enrollment for backup YubiKeys and lost YubiKey recovery mechanisms.
These features make this application the most robust authentication tool that Yubico has provided for standalone Windows computers.
The preview program gives participants the ability to download the new Yubico Login for Windows Application, test the application, and provide feedback on the experience. This is your chance to influence the features prior to the upcoming official release.
The Yubico Login for Windows Application is best suited for:
- Individuals that have local accounts on Windows 7, Windows 8.1 or Windows 10 computers.
- Individuals or organizations that prefer local accounts created on their computers in order to keep sensitive information localized as opposed to taking advantage of a more connected Windows 10 experience (such as using Outlook.com, OneDrive, Live.com, Hotmail.com etc.).
- Organizations that have a mix of Windows 7 and Windows 10 computers and do not use Azure Active Directory or Active Directory.
The Yubico Login for Windows Application is not ideally suited for:
- Users who typically log into Windows computers with a Microsoft Account (e.g. username@outlook.com, username@hotmail.com, username@live.com, etc.).
- Users who utilize the following sign-in options for their local account: Windows Hello (face, fingerprint, or iris), PIN, or picture password.
If you are interested in joining the public preview program for Yubico Login for Windows Application please sign up here. The preview offering and a configuration guide will be made available after sign-up.



