Firefox Quantum is the latest internet browser to natively support FIDO Universal 2nd Factor (U2F) devices, and we couldn’t be more thrilled to see this advancement! With Mozilla jumping on board, millions of Firefox users can now begin to experience the ease-of-use and security of the YubiKey and U2F authentication…with one small caveat. FIDO U2F is not turned on by default in the Firefox browser.
If you’re among the individuals testing the FIDO U2F YubiKey with Firefox Quantum, you’ve likely already experienced a few common challenges. First, FIDO U2F is not a default setting with the latest Firefox browser. It requires configuration in advanced settings. Second, even after enabling FIDO U2F, some services may not recognize it. We understand that this can be frustrating or inconvenient for users, and as a principal inventor of the FIDO U2F open authentication standard, we’d like to provide additional clarity and guidance.
Why isn’t FIDO U2F a default setting in Firefox Quantum?
Mozilla plans to only support the out-of-the-box experience with FIDO U2F devices using Web Authentication APIs (as part of FIDO 2) versus FIDO U2F APIs. Per the company’s Security/Crypto Engineering wiki page, they intend to “…permit use of U2F tokens via a user-controllable preference (not on by default) in Firefox 56 or 57 (Done in Firefox 57), and Web Authentication (on by default) in Firefox 59 or 60.”
In many ways, FIDO 2 is the next-generation of FIDO U2F, as it will pave the way for things like multi-factor and passwordless login, while still supporting two-factor authentication (2FA) functionalities of the original FIDO U2F standard. As Web Authentication specifications will likely not be complete until early 2018, users will need to wait for the seamless experience with U2F devices in Firefox until the Web Authentication API integration is done.
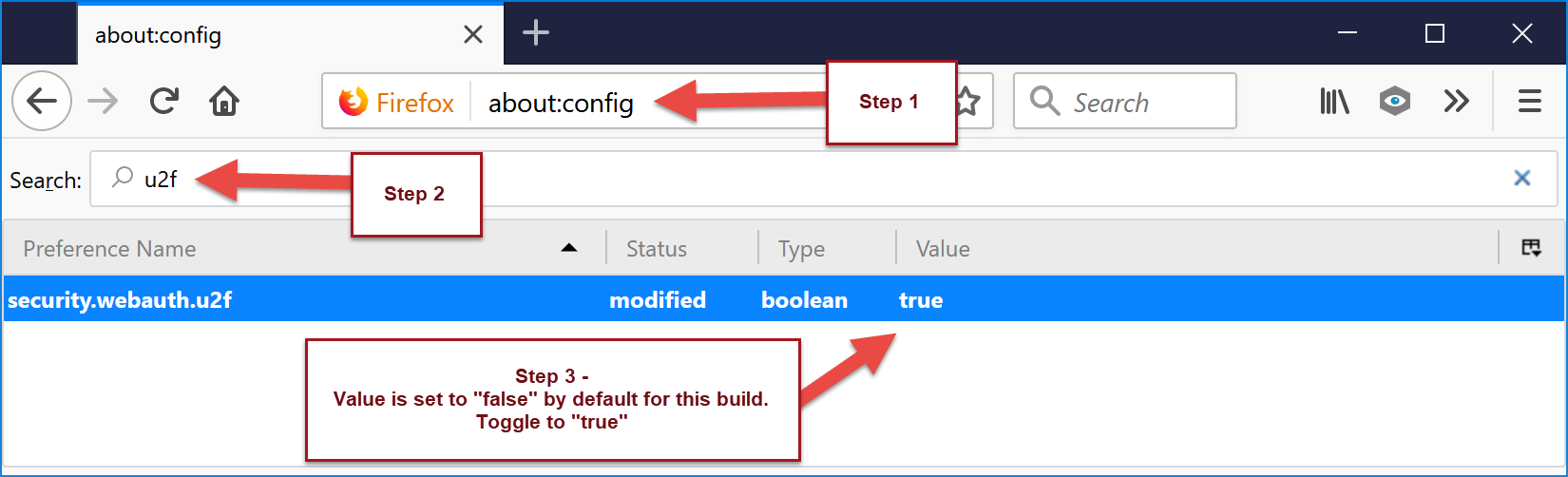
How do I enable FIDO U2F in Firefox Quantum?
While the FIDO U2F experience in Firefox is limited at the moment, turning it on is very simple. It only takes three steps.
1. Type about:config into the Firefox browser.
2. Search for “u2f”.
3. Double click on security.webauth.u2f to enable U2F support.
Even after enabling FIDO U2F in Firefox Quantum, why won’t YubiKeys work for some U2F-enabled sites?
Integrating with FIDO U2F v1.1 JS API will allow a developer’s web app to support U2F on Firefox. That said, it’s important to understand that every FIDO U2F implementation can vary from the official specifications. For example, Mozilla did not fully implement the FIDO AppID and Facet Specification. Some sites supporting FIDO U2F have made accommodations for the incompleteness of Firefox’s implementation, but some have not. In other situations, some services may not work with Firefox Quantum because of a service-specific implementation. For this reason, Firefox Quantum users are currently having trouble authenticating with their FIDO U2F devices for some sites that typically support FIDO U2F devices. Our recommendation? Make a request to both Mozilla and that particular service to refine their FIDO U2F support, allowing for Firefox compatibility.
Ultimately, Mozilla’s FIDO U2F support is a huge progression toward strong, unphishable authentication. We can only hope to see the platform’s FIDO U2F authentication experience grow to become seamless and simple as the FIDO standard intends.
5.9.18 Update – Firefox 60 is the first browser to support the new security standard, FIDO2, Web Authentication (WebAuthn) and U2F.



