Resources
Browse our library of white papers, webinars, case studies, product briefs, and more.
-

Stop enterprise-wide identity phishing with modern strong authentication: Why mobile authentication just isn’t good enough TY Thank you for your interest in our white paper, Stop enterprise-wide identity phishing with modern strong authentication: Why mobile authentication just isn’t good enough Read more -

Modern strong authentication and compliance for Financial Services: How the YubiKey meets global Financial Services regulations TY Thank you for you interest in our eBook, Modern strong authentication and compliance for Financial Services: How the YubiKey meets global Financial Services regulations. Read more -

How State and Local Governments are Combating Account Takeovers: A Government Technology Case Study TY Thank you for you interest in our white paper, Enhancing Cybersecurity in the Public Sector: How State and Local Governments Are Combating Account Takeovers with Hardware Security Keys Read more -

Getting Started with Strong Authentication in Financial Services: Best practices for implementing the YubiKey for fast, easy, and strong authentication TY Thank you for you interest in our white paper, Getting Started with Strong Authentication in Financial Services: Best practices for implementing the YubiKey for fast, easy, and strong authentication. Read more -

Establishing a Secure Portable Root of Trust with WebAuthn TY Thank you for you interest in our white paper, Establishing a Secure Portable Root of Trust with WebAuthn. Read more -
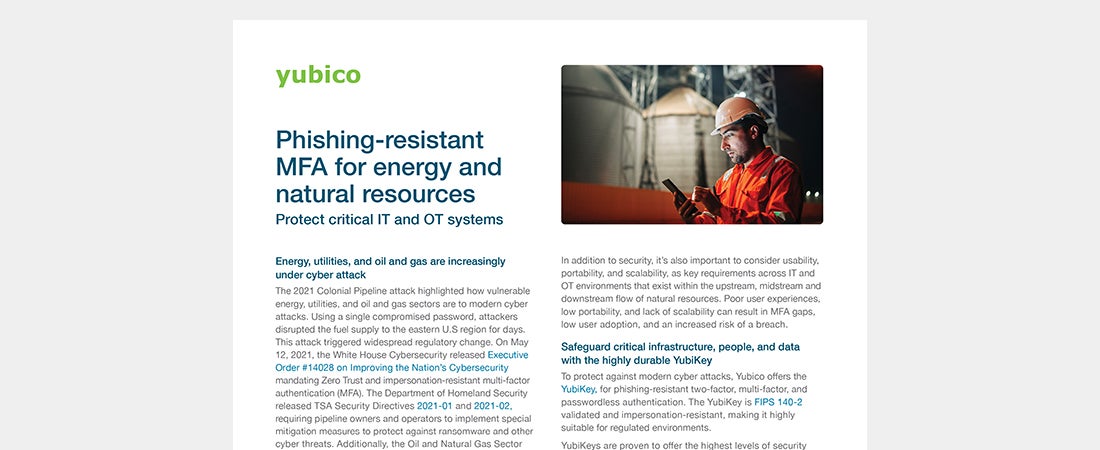
Save energy and natural resources with phishing-resistant MFA Learn how the YubiKey protects critical IT and OT systems and provides highest-assurance security for your invaluable resources in the energy, utility, oil and gas sectors. Read more -

Cybersecurity in the Work From Anywhere Era: Findings on Employee Attitudes and Adaptability to At-Home Corporate Security TY Thank you for you interest in our white paper, Cybersecurity in the work from anywhere era: Findings on employee attitudes and adaptability to at-home corporate security. Read more -

Combat Ransomware: Strong authentication best practices to defend against threats TY Thank you for you interest in our white paper, Mitigate ransomware risks: The critical role of strong authentication and modern MFA. Read more -

Bridge to Passwordless: Separating fact from fiction in your journey TY Thank you for you interest in our white paper, Bridge to Passwordles: Separating fact from fiction in your journey. Read more