What is a Passkey?
Passkeys are a passwordless authentication method that uses public-private key cryptography and biometric verification to provide stronger security than traditional passwords while offering a simpler user experience through secure storage on devices, in the cloud, or on hardware security keys.
Passkeys pave the path to passwordless authentication – a move away from passwords, often the cause for 80% of breaches today. Passkeys, based on modern authentication protocols, and public key cryptography, not only can displace traditional passwords but also other weaker authentication methods.
This article will further explore the nuances of passkeys, covering their technical mechanisms, different types, significant security advantages, and practical applications in modern authentication.
Passkeys: a more detailed look
Passkeys use securely stored digital keys, eliminating the need for users to remember complex passwords or supplement login using a One-Time Password (OTP). These storage locations include:
- In the cloud with trusted service providers
- On devices themselves, like phones and laptops
- On dedicated hardware security keys, which provide the greatest security since they provide physical separation from software and use dedicated secure elements
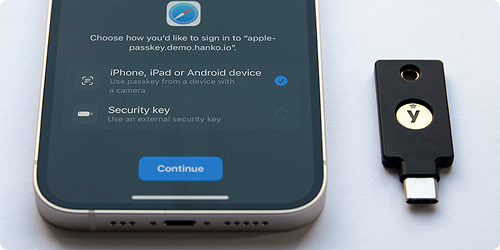
Because of not having to remember complicated words or phrases, and the fact that passkeys are stored safely in the cloud with trusted service providers, or even right on the devices themselves, it makes it much harder for hackers to compromise user accounts through social engineering or phishing attacks. Once set up, the signing-in process only involves simple biometric authentication like a fingerprint, or tapping a hardware security device, making it a super simple user experience while reducing common attack vectors like credential stuffing, password reuse, and remote phishing.
Even though passkeys can greatly simplify and secure the account login process, physical device access or sophisticated malware could still pose risks if passkeys are not set up correctly. Using passkeys on security keys as a way to set up and secure all other passkeys can reduce these additional risks.
The term “passkey” is a clever amalgamation of the words “password” and “key”, created to convey that it can be used to login as easily as the common password, but with much greater security, such as that offered by a door locked by a key. Unlike securing accounts with something weak such as a password, which can be guessed, stolen or phished, passkeys use a mathematical link between two unique digital codes to authenticate, namely a public and private cryptographic key pair.
Using well known cryptographic algorithms, the public key can be used to verify that any given digital signature has been derived from its uniquely paired private key – and only that private key – without ever needing to know or have the user expose the private key.
Moreover, passkey is not a new technology, but is actually based on the widely recognized FIDO2/WebAuthn protocols, that have been in active development and use for many years. They do however, represent the cybersecurity industry’s attempt to unify, streamline, and modernize these existing authentication methods to provide stronger and easier to use protection against threats to authentication to a wider audience.
How do passkeys work?
Here’s how it works, assuming a passkey has already been registered:
- When a user attempts to sign into a service, that relying party initiates the authentication process by generating a random cryptographic ‘challenge’ (sometimes referred to as a nonce) and sends it to the user’s device.
- The user’s device then responds by using its private key to derive a digital signature from that specific challenge.
The relying party then validates this digital signature by applying a complementary mathematical operation using the public key in its possession. This operation mathematically confirms that the signature was indeed created by the corresponding private key for that specific challenge.
If the verification succeeds, access is granted.
This process ensures that only the singular private key, uniquely stored on the secure element on the user’s device, could have been used to successfully create the digital signature. Any other key or value would cause the cryptographic proof to fail since the result would not correspond to the expected value using the stored public key. It’s important to note that any local authentication on the user’s device, such as a PIN or biometric authentication, only occurs locally to authorize the use of the private key for digital signature creation, and is not part of any data exchanges between the relying party and the user.
What are the different types of passkeys?
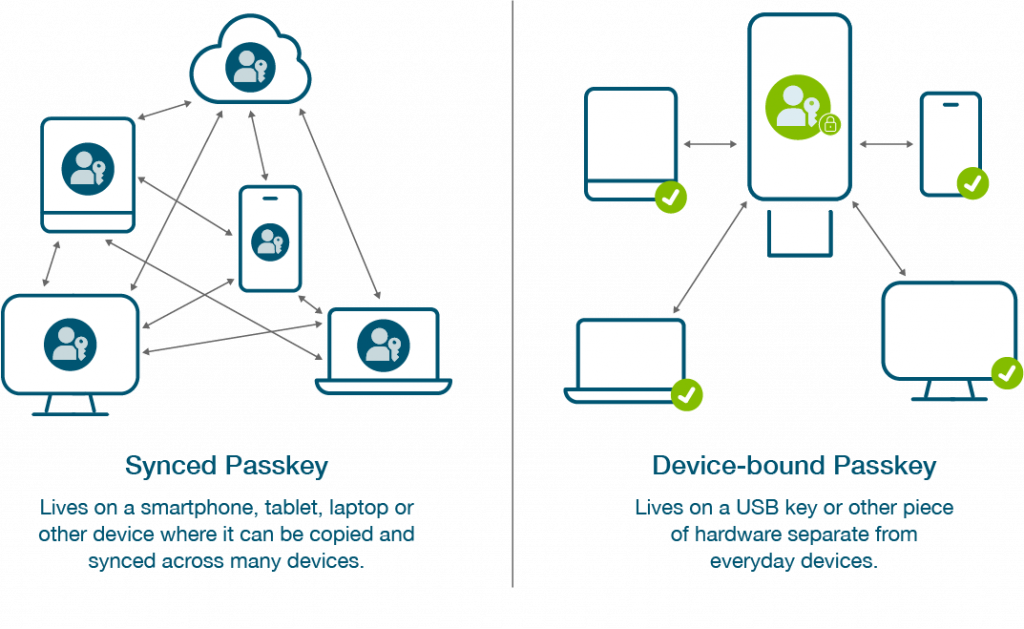
There are two sub-types of passkeys, namely synced passkeys and device-bound passkeys. As the technology evolves, there will likely be other differences or divergent approaches with how passkeys work and unique to various vendors in the future, since broad consensus has yet to coalesce around passkey best practices and levels of assurance. However, the issue of where the private key resides will likely be the biggest and most important difference between passkey implementations.
Synced passkeys
Synced passkeys live in the cloud, which means credentials associated with an account can be shared and distributed between smartphones, tablets and laptops. The most obvious examples of synced passkeys are what large technology providers such as Apple, Google, and Microsoft have implemented for their users. While synced passkeys enable easier account recovery in the case of a lost or stolen device, the FIDO credential is harder to track, so it is most suitable for lower security assurance scenarios.
To illustrate with an example, Apple stores private keys in a user’s iCloud keychain where it can then be accessed by any other authorized device. This type of passkey login makes access especially easy, since the passkey can traverse between devices through an encrypted channel and can be easily restored even if a device is lost or a new one is introduced. It does, arguably, compromise security in the process by adding a potential new vector of attack, since hackers could potentially breach the cloud account (or password manager in other instances of shared passkeys) unless there is phishing-resistant two-factor authentication in place there as well.
Device-bound passkeys
Device-bound passkeys reside on physical hardware, and cannot be copied, shared or synchronized through a cloud service. The devices in question include almost any hardware with a secure element. Device-bound passkeys offer compliance with the most stringent requirements across industries, do not depend on the security of a third-party service and are therefore better suited for the enterprise or use cases requiring maximum security. Flexibility suffers somewhat compared to synced passkeys, since each new device must be registered separately before it can be used for authentication, but the trade off is that security improves significantly when the only way to authenticate is by physically possessing a specific, previously registered device – no device, no access.
Device-bound passkeys in modern hardware security keys offer the highest security assurance and provide enterprises with trusted credential lifecycle management and attestation abilities. In security, attestation refers to the process of providing evidence, often cryptographic, to verify the integrity, authenticity, and compliance of a system, software, or identity. It’s a way to prove that a system is in a known good state and hasn’t been tampered with, or that the credential is legitimate and hasn’t been altered. With this high assurance and trusted passkey approach, organizations can deliver the simplest user onboarding and credential recovery experience across devices and platforms, all while staying in compliance with the most stringent requirements and regulations. Setting up, or bootstrapping, any other type of device-bound passkey with a hardware security key ensures that the solution is stronger and more secure.
Device-bound passkeys can also be built-in on modern everyday devices such as smartphones and laptops and offer enterprises and their users an easy and convenient way to use passkey technology where passkeys stay local to their device
While synced passkeys are a new term to enter the collective lexicon, device-bound passkeys are technically a synonym for discoverable FIDO2 credentials and have been supported as far back as 2018, by the YubiKey 5 Series for example.
Can you share passkeys?
Synced passkeys are shareable credentials that can travel across various devices such as smartphones, laptops, and tablets connected to a user cloud account. These passkeys are more consumer-grade, and are universally accepted to be unsuitable for enterprises creating chilling failure points due to the higher potential for compromise. By contrast, device-bound passkeys have a few variations themselves and are all enterprise-grade.
Sharing passwords makes it hard to track if a legitimate user accessed an account, and makes it difficult to track. Similarly, while passkeys are more phishing-resistant than passwords, the ability to copy and share synced passkeys can create similar failure points as shared passwords do, preventing trackability if pre-designated users authenticated into and accessed specific accounts. With synced passkeys, while there is convenience for a user to have seamless access across all their personal devices, it’s important to note that if the underlying cloud account itself is shared between two or more designated users, the synced passkeys associated with that account would also become accessible to all users of that shared account. This could create an attack vector for hackers, and is a distinct possibility due to the nature of cloud account sharing.
Why are passkeys important?
The biggest digital service and identity providers are all investing in passkey technology, in addition to many other tech companies large and small, highlighting its growing importance as an authentication standard. But what makes passkey technology crucial in the digital era? Mostly because passwords are:
- Easy to forget, especially as they get more complicated with regards to minimum accepted requirements (e.g. 8 character minimum length with a mix of upper case, lower case, special characters and numbers).
- Relatively easy to guess or steal, and users can be tricked into exposing them through phishing or social engineering.
- Commonly recycled by users across multiple services, creating a situation where attackers can potentially compromise a multitude of accounts from a single breach.
There has long been a push within the security industry to replace passwords with something that makes authentication both easier to accomplish yet harder to exploit. Passkeys do exactly that:
- Since users do not have to remember or type anything, there is nothing to forget or expose at login.
- There is no need to constantly cycle or change the underlying mechanism, as may be the case with passwords.
- As the underlying technology is based upon public key cryptography, it is essentially impossible for attackers to steal or phish the information needed for login.
The creation, evolution, and now maturation of passkey technology is important for all because it means passwords can eventually be retired, and pave the way for passwordless logins that are regarded by experts as superior in both security and usability.
Why are passkeys so phishing-resistant?

Passkeys pair a public key with an unguessable private key which is never shared.

Every credential is tied to a real URL, which can be verified as legitimate or not.

Every credential is registered to a real human, blocking bots or other remote attackers.
Who needs passkeys?
Essentially, anyone looking for a simpler, stronger and safer way to manage their online identity can benefit from passkeys. For individuals, this means no more struggling to remember complex passwords or falling victim to sneaky phishing emails that try to steal login credentials. For businesses, adopting passkeys can significantly reduce the risk of costly cyberattacks, protect sensitive data, and slash the burden of password-related help desk calls. While there is clear value for everyone to transition away from traditional passwords as an authentication mechanism, both organizations and individuals who are already more invested in cybersecurity will find the transition especially beneficial.
While there are currently no formal universal mandates for passkey usage, the industry is clearly moving in this direction. As a prime example, Microsoft has aggressively pursued a passwordless future, making passwordless authentication the default for new Microsoft accounts and actively encouraging existing users to transition away from passwords, including by ending password storage functionality in its Authenticator app. This follows a broader trend of pushing for stronger authentication standards, such as the general adoption of multi-factor authentication (MFA) across many services by security experts, the U.S. White House’s mandate for phishing-resistant MFA within the Federal government, or the development of a unified electronic ID scheme within the EU. Given these precedents, it’s easy to imagine future requirements to use passkeys emerging by law, under contract, or as a key stipulation for enterprises to be covered under cyber insurance. Although global passkey adoption is still relatively small, all the necessary components are in place, and momentum is rapidly building for passkey technology to become the new standard for online authentication.
Benefits of Passkeys
Passkeys offer a multi-faceted improvement over traditional passwords, delivering significant advantages for both individuals and organizations:
- Improved Accessibility: Passkeys significantly enhance ease of use by replacing complex, easily forgotten, or often exploited passwords with a digital credential. Whether stored securely in the cloud or directly on a device, access becomes as simple as a swipe, press, tap, or a quick biometric gesture. For example, using a YubiKey as a passkey often involves just a simple tap or touch of the hardware security key, providing immediate and convenient login without the need for typing or remembering a single character.
- Increased Security: At their core, passkeys leverage strong public key cryptography, making credentials far harder to exploit and significantly reduces the likelihood of unauthorized access. This robust mathematical foundation makes authentication difficult to break, even with immense computing power and resources. Credential exploitation remains a primary vector for cyberattacks but passkeys drastically shrink the risk. Device-bound passkeys, such as those provided by a YubiKey, offer an even higher level of security by storing the private key in a tamper-resistant chip, making them virtually immune to sophisticated phishing attacks and malware.
- Efficient Access Management: As cyberattacks become more common and digital transformation accelerates, managing user identities and access becomes an increasing headache for both users and enterprise security teams. Passwords specifically, are rapidly proving themselves to be insufficient with the demands of modern IT. Passkeys represent a viable and superior alternative with a clear path to adoption, streamlining login processes and significantly reducing administrative overhead. Organizations deploying YubiKeys for passkey authentication, for instance, can simplify their security infrastructure, reduce help desk calls related to password resets, and enhance overall operational efficiency for secure access, freeing up resources for other critical tasks.
Passkey best practices
Even though passkey technology is still evolving towards full maturity and widespread adoption, several key best practices are already emerging. These practices are crucial for both individuals and organizations to maximize the benefits and ensure secure, seamless authentication, especially as the user base grows and use cases expand.
- Prioritize enabling passkeys: For individuals, the most immediate best practice is to activate passkeys wherever the option is available for online services. For organizations, it’s essential to prioritize enabling passkey support for users across all relevant applications and services. This directly leverages the strongest phishing-resistant authentication methods currently available, moving away from vulnerable passwords.
- Secure your local device: Since passkeys are intrinsically tied to the device they are created on (whether an Android phone, laptop or hardware security key), securing that device itself is paramount. Implementing strong local authentication, such as robust biometric authentication (fingerprint, facial recognition) or a complex PIN, directly protects the private key that your passkeys rely on. Without local device security, the passkey’s effectiveness is compromised.
- Understand syncing and recovery strategies: Be aware of how synced passkeys (e.g. Apple iCloud Keychain, Google Password Manager) provide convenience across multiple devices. While incredibly useful for a single user, understanding that sharing the underlying cloud account could grant unintended access to synced passkeys as well. It’s paramount to establish robust account recovery methods beyond passkeys themselves, such as using backup FIDO2 security keys for critical accounts, or alternative secure recovery flows.
- Plan for a phased transition, including education: For enterprises, a strategic, phased transition away from passwords is more effective than an abrupt cutover. This involves offering passkeys as an option alongside existing password or multi-factor authentication methods, gradually encouraging and guiding user adoption. Providing clear education and communication to users about what passkeys are, their benefits, how to create them, and how to use them is crucial for minimising confusion and ensuring successful deployment.
- Build a passkey-friendly ecosystem: Both users and enterprises should begin thinking about building an ecosystem that makes passkey adoption and management easy. For users, this might mean using a passkey manager or ensuring consistent passkey support across their chosen devices. For organizations, it means ensuring their platforms and identity providers are compatible with WebAuthn standards, streamlining the registration and authentication experience, and supporting the diverse range of passkey types their users might employ. This approach simplifies the overall identity and access management landscape.
How to choose a Passkey solution
Selecting the right passkey solution, like the YubiKey, for an individual or an organization requires striking a careful balance between robust security and seamless accessibility. Overemphasising security can inadvertently lead to arduous login processes, while neglecting security for pure convenience can leave accounts vulnerable to fraudulent access. The ideal passkey strategy is one that aligns with specific needs, risk tolerance, and operational environments.
Here’s a high-level process to help guide the selection of a passkey solution:
- Identify needs and risk profile. The first crucial step is to assess the specific security requirements and user experience preferences. Consider the following:
- What level of security is paramount? Is the data being protected highly sensitive (e.g. financial records, patient data, intellectual property) or more general-purpose?
- What is the potential impact of a security breach? How severe would the financial, reputational or operational consequences be?
- What is the risk tolerance of the organization or individual? Is there a willingness to accept minor inconveniences for maximum security, or is user experience a higher priority?
- How many devices do users typically operate? Is cross-device synchronization a critical requirement for convenience?
- For organizations, industries like government, finance, healthcare, energy, pharma, and manufacturing, which face high-stakes threats and stringent compliance mandates, typically place a premium on the highest levels of security assurance.
- What level of security is paramount? Is the data being protected highly sensitive (e.g. financial records, patient data, intellectual property) or more general-purpose?
- Understand the different types of passkeys available. As detailed in the “What are the different types of passkeys?” section, passkeys primarily fall into two categories, each offering a distinct balance of convenience and security:
- Synced passkeys: These offer high accessibility and user convenience by allowing private keys to synchronise across multiple devices via a cloud service. They are excellent for everyday use and easy recovery.
- Device-bound passkeys: These offer the highest level of security by tethering the private key to a specific, tamper-resistant device (like hardware passkeys that reside in a YubiKey). They provide superior protection against phishing attacks and malware, making them ideal for high-security environments, though they offer less flexibility and convenience. Understanding this core trade-off between seamless cross-device access and ultimate security is fundamental to making an informed choice.
- Synced passkeys: These offer high accessibility and user convenience by allowing private keys to synchronise across multiple devices via a cloud service. They are excellent for everyday use and easy recovery.
- Choose the right passkey type (and solution provider). Based on the identified needs and the suitable type of passkey, an informed decision can be made:
- For high-security needs: organizations or individuals with a low risk tolerance for cyberattacks, particularly those handling highly sensitive data or operating in critical sectors, will benefit most from device-bound passkeys. Solutions utilising hardware security keys like YubiKeys are often preferred due to their tamper-resistant storage of the private key and strong phishing-resistant properties, providing the highest security assurance.
- For balanced security and convenience: organizations or individuals primarily seeking to significantly upgrade security while prioritizing seamless login experiences across multiple devices may prefer synced passkey solutions. These offer a strong improvement over traditional passwords, but remember that it is vital to also secure the underlying cloud account with strong multi-factor authentication to mitigate potential vulnerabilities associated with cloud key storage.
- Many organizations may find a hybrid approach beneficial, deploying device-bound passkeys for privileged users or critical systems, while offering synced passkeys for general workforce or less sensitive applications.
- For high-security needs: organizations or individuals with a low risk tolerance for cyberattacks, particularly those handling highly sensitive data or operating in critical sectors, will benefit most from device-bound passkeys. Solutions utilising hardware security keys like YubiKeys are often preferred due to their tamper-resistant storage of the private key and strong phishing-resistant properties, providing the highest security assurance.
- Re-evaluate when requirements change. The landscape of cybersecurity threats, technological advancements, and organizational needs is constantly evolving. Therefore, the chosen passkey solution should not be a static decision. It’s a best practice to periodically:
- Review your risk profile: Has the threat landscape changed enough to merit a security change? Or perhaps there are new compliance requirements.
- Assess new passkey capabilities: Has the technology matured in ways that better suit the underlying needs or offer improved features?
- Gather feedback: Are there new pain points or opportunities for improved user experience? Regular re-evaluation ensures the chosen passkey strategy remains effective, efficient, and aligned with the security posture and operational demands.
- Review your risk profile: Has the threat landscape changed enough to merit a security change? Or perhaps there are new compliance requirements.
Does Yubico support passkeys?
Not only does Yubico support passkeys, we have also been a pioneer in this field and a major force behind the development and adoption of FIDO2, the underlying protocol used within passkey technology. Yubico has worked closely with the FIDO Alliance since the beginning, to develop the authentication protocols and bring these innovations into the product sphere.

Our signature product, the YubiKey, is a security key that plugs into a USB port or read by an NFC reader, to authenticate both the user and the device it’s plugged into. YubiKeys can handle authentication through multiple means: two-factor, multi-factor, and touch-to-sign. Further, with our latest iteration, the YubiKey 5 Series, our security keys even offer passwordless authentication using passkeys.
The YubiKey works as a passkey generator that can create both the public and private keys necessary to begin passkey login with accounts, apps, services and vendors that enable it – a YubiKey serves as a repository for up to 25 unique passkeys. These are device-bound passkeys, meaning they live only on a particular YubiKey, and thus the only way to gain unauthorized access would be to steal the physical YubiKey itself and then complete the authentication ceremony with either the correct PIN or biometric – a near impossible sequence of events for online attacks and an extremely unlikely sequence for offline attacks. This resilience represents the gold-standard in passkey security while simultaneously making it easy to manage passkeys for multiple logins.
We recommend a proven best practice as you begin your passkey journey
1. Put your credential on a portable device such as a YubiKey
2. Use the portable YubiKey to set up your local credential on Microsoft Authenticator or Windows Hello or Windows Hello for Business.
Learn more about how device-bound passkeys strengthen security.

FAQ
Passkeys achieve a higher level of security primarily by eliminating the vulnerabilities inherent in passwords themselves. Even the strongest password can be phished, keylogged, or exposed in a data breach. Passkeys, by contrast, use public key cryptography where the private key never leaves the device or cloud service provider, and is never transmitted to the relying party. When authenticating, the device performs a cryptographic signature using the private key, which the relying party verifies with its corresponding public key. This process is inherently phishing-resistant because the passkey is also cryptographically bound to the legitimate website or service, and simply won’t work on a fraudulent site. Furthermore, unlike SMS 2FA, which can be intercepted via SIM-swapping attacks, a passkeys’ possession factor is tied directly to your secure device and its local authentication, such as with biometric authentication.
Device-bound passkeys offer the highest security because their private key is securely stored on a specific physical device (e.g. a YubiKey or a phone’s secure element) and cannot be copied or synced. If you lose that device, the private key remains secure on the lost device, protected by its physical possession and the local device unlock method (PIN or biometrics). An attacker finding the device would still need to bypass the device’s security for starters, and even then, would need to guess which online services or accounts have been associated with the device. To regain access to accounts, the typical action is to use a pre-registered backup method. This could involve another previously registered device-bound passkey, a synced passkey, or a robust account recovery process provided by the relying party that might involve identity verification or recovery codes. The key is to establish these backup methods before a device is lost.
Yes, organizations can and often do enforce stronger authentication methods, including specific types of passkeys. Using FIDO2/WebAuthn standards, a relying party can specify its requirements for passkey creation during registration. For instance, an organization might configure its identity provider to only accept passkeys attested as being hardware-backed (e.g. from a YubiKey) for access to sensitive systems or for privileged user accounts. This allows them to mandate the highest level of security assurance where it’s most critical, while potentially allowing more convenient synced passkeys for lower-risk internal applications, creating a tailored security posture.
When using a passkey from a phone to log into another device or service, the private key itself does not leave the device. Instead, the phone acts as the “authenticator.” The device sends the cryptographic “challenge” to the phone, and the phone’s private key generates the digital signature locally. This signature is then securely transmitted back to the device (usually via an encrypted channel), which forwards it to the relying party for verification. This process ensures the private key’s immobility while still providing a convenient cross-device experience.