Phishing-resistant users: The next evolution in authentication
Your journey towards cyber resilience begins and ends with the YubiKey
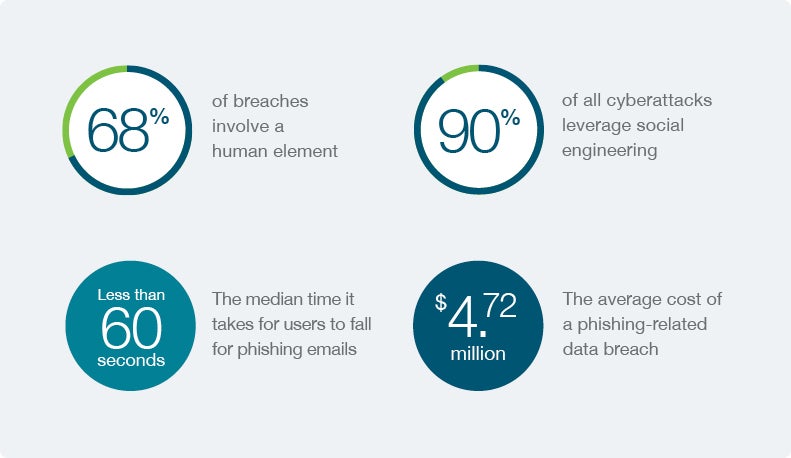
Enterprises face constant cyber threats
Enterprises’ registration, authentication, and recovery processes are prime phishing and social engineering targets because cybercriminals have found effective ways to exploit the organization’s weakest link: gaps in the credential lifecycle.
MFA isn’t enough
Many organizations who have implemented multi-factor authentication (MFA) in some form believed it would effectively prevent account takeovers, but their authentication processes have remained vulnerable to phishing attacks. That’s because not all MFA is created equal. Attackers have found new ways to exploit vulnerabilities in some two-factor methods, leaving enterprises scrambling for stronger protection.
For ultimate protection, shift from phishing-resistant authentication to phishing-resistant users
Phishing-resistant authentication is only effective when it moves effortlessly with the user:

By safeguarding registration, authentication, and recovery across all devices, platforms, and processes with purpose-built, portable hardware security keys, such as YubiKeys, enterprises build the highest-assurance foundation to combat evolving threats.
Cultivate phishing-resistant users in three steps:
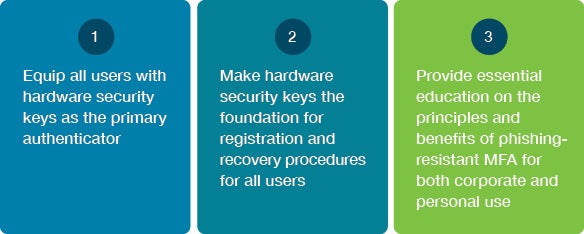
With the YubiKey for modern authentication, organizations can drive business continuity, be cyber resilient, satisfy cyber insurance and regulatory requirements, all while ensuring the best security and user experience for employees and end-customers alike. By properly equipping all their users with the most secure phishing-resistant MFA available, enterprises minimize reliance on users to make security decisions and effectively safeguard sensitive data and operations.
Why choose the YubiKey for phishing-resistant authentication?

- Provide secure user access at scale on any device with the best user experience
- Does not need battery or cellular connectivity to function
- Bridge to modern passwordless with multi-protocol support for Smart Card/PIV, FIDO2/WebAuthn, FIDO U2F, OTP and OpenPGP on a single key
- Deploy the most secure passkey strategy: device-bound that is purpose-built for security, FIPS 140-2 validated and Authenticator Assurance Level 3 (AAL3) compliant
- Drive regulatory compliance to BSI-KritisV, CCPA,E8MM, eIDAS, FedRAMP, FERC, GDPR, NERCCIP, NIS2 Directive, PCI DSS 4.0.1, PSD2, SOCI Act, SOC2, SOX, TSA.
The cornerstone of building resilience lies in fostering a culture of phishing-resistant users. Your journey towards true cybersecurity begins and ends with the YubiKey.